Last week’s unprecedented ransomware cyber attacks (http://preview.tinyurl.com/lhjfjgk) caught me working through some research on security automation. The cyber attacks evidently were attributed to an unpatched Windows XP vulnerability. When challenged with securing 1,000s of assets such as all the Windows desktops and Linux servers in an organization, automation quickly becomes a requirement.
Automation is increasingly coming up in our client conversations about how to secure the technology ‘stack’ supporting large ERP implementations such as the Oracle E-Business Suite, PeopleSoft, and SAP. For example, how do you from a security professional perspective, communicate an objective risk assessment comprehensive of both the secure baseline configuration (control adherence/violation) and security patch levels (patch/unpatched CVEs) for the Linux operating systems, virtualization software, web server, database and the ERP application itself? Without automation, it is not feasible to promptly produce risk-based assessments of the complete technology stack and to produce results that are readily expressed in a common risk measurement (e.g. CVE) not requiring deep subject matter expertise.
Automation, however, can only be considered after requirements have been defined. I have long used Security Technical Implementation Guides (STIGs) in both my research and work with clients to define security requirements. STIGs are secure configuration standards developed by the US Department of Defense for products such as the Oracle RDBMS and are freely available (http://iase.disa.mil/stigs/Pages/index.aspx). While most clients do not need their databases hardened to military specifications, STIGs are an invaluable source of security best practice thinking.
STIGs (security checklists) are only available in xml format – not PDF files. DISA does provide a utility to view and work with STIGs (http://iase.disa.mil/stigs/Pages/stig-viewing-guidance.aspx) which allows you to manually execute the checklist, record your findings and then export the results. See this YouTube (https://www.youtube.com/watch?v=-h_lj5sWo4A) posting for a great summary of the STIG Viewer and how to use it.
Security Content Automation Protocol (SCAP)
To answer the question of how do you automate STIG and/or security checklists, again the Department of Defense has thought through the challenges and has created the Security Content Automation Protocol (SCAP).
SCAP is a multi-purpose framework to automate the security scanning of configurations, vulnerabilities, patch checking and compliance. SCAP content is developed by the National Institute of Standards and Technologies (NIST) and the components are described in the table below. The key point is that SCAP security content (checklists) is free and that the SCAP content scanning tools are available both in open source and commercial options.
|
SCAP Component |
Description |
| eXtensible Checklist Configuration Description Format (XCCDF) | XML-based language for specifying checklists and reporting the results of checklist evaluations. |
| Open Vulnerability and Assessment Language (OVAL) | XML-based language for specifying test procedures to detect machine state |
| Common Vulnerabilities and Exposures (CVE) | Nomenclature and dictionary of security-related security flaws |
| Common Configuration Enumeration (CCE) | Nomenclature and dictionary of software security configuration issues |
| Common Vulnerability Scoring System (CVSS) | Methodology for measuring the relative security of software flaws |
| Open Checklist Interactive Language (OCIL) | XML-based language for specifying security checks that require human interaction or that otherwise cannot be bundled by OVAL |
| Asset Reporting Format (ARF) | Standardized data model for sharing information about assets to facilitate the reporting, correlating, and fusing of asset security information. |
OpenSCAP
There are many tools, Integrigy’s AppSentry included (https://www.integrigy.com/products/appsentry), that will perform a STIG scan of an Oracle database. The question I was researching this week, is could I use a single SCAP tool to automate the scanning of both the Linux server and the database as well as possibly ERP configurations for PeopleSoft and/or the Oracle E-Business Suite – can could I possibly do this with open source software?
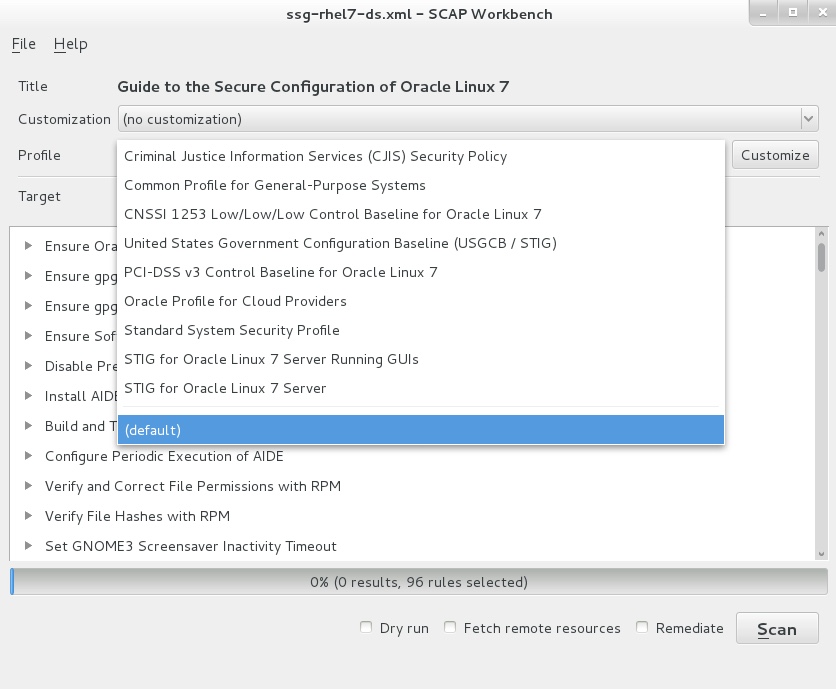
The first tool I considered was OpenSCAP (https://www.open-scap.org/). This open source tool is easy to install either on your laptop or Linux database server and has remote scanning capabilities. The example below shows the capabilities of the GUI tool ‘SCAP Workbench’ and the freely available content that is installed by default for scanning a Linux server.
This exercise quickly confirmed that there is a great deal of security automation available for Linux system security configurations. Here, though, is where I hit a wall: could OpenSCAP work with Oracle databases? While the SCAP standards clearly showed support for scanning SQL database configurations using OVAL’s SQL probes (e.g. sql_test, sql57_test etc…), I may be corrected, but the standard build of OpenSCAP do not appear to include the SQL probes.
JOVAL
To obtain the SQL probes for SCAP scanning of database configurations, after some research, I obtained an evaluation copy of Joval Professional (http://jovalcm.com/). Joval describes themselves as allowing you to Scan anything from anywhere and to allow continuous configuration assessments for developers, enterprises, content authors and security professionals.
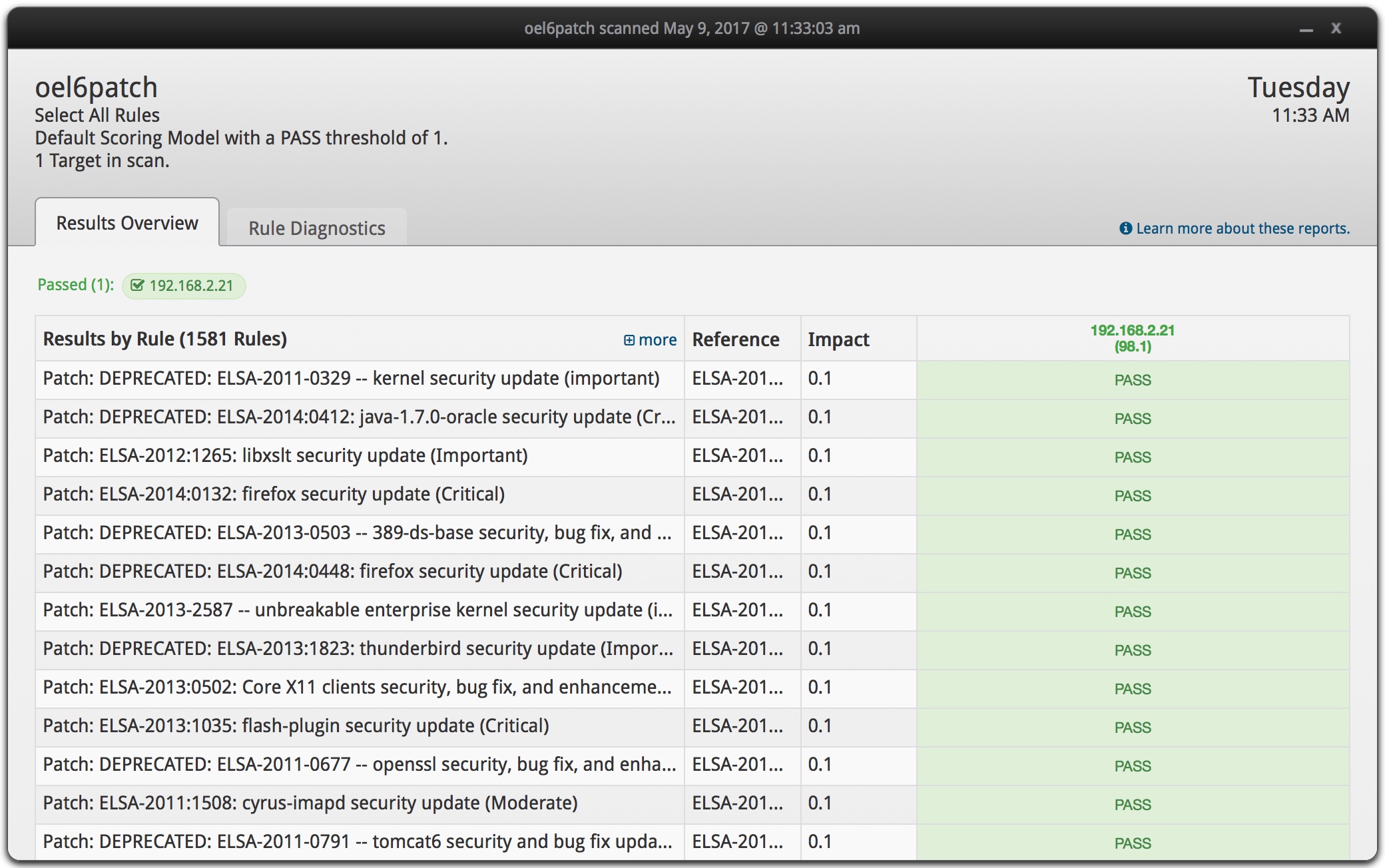
The installation of Joval Professional was quick and I was able to scan my laptop and remotely scan the remote Oracle Linux server without issues. The screen shot below shows the results of the remote scan of the Linux server running the Oracle RDBMS.
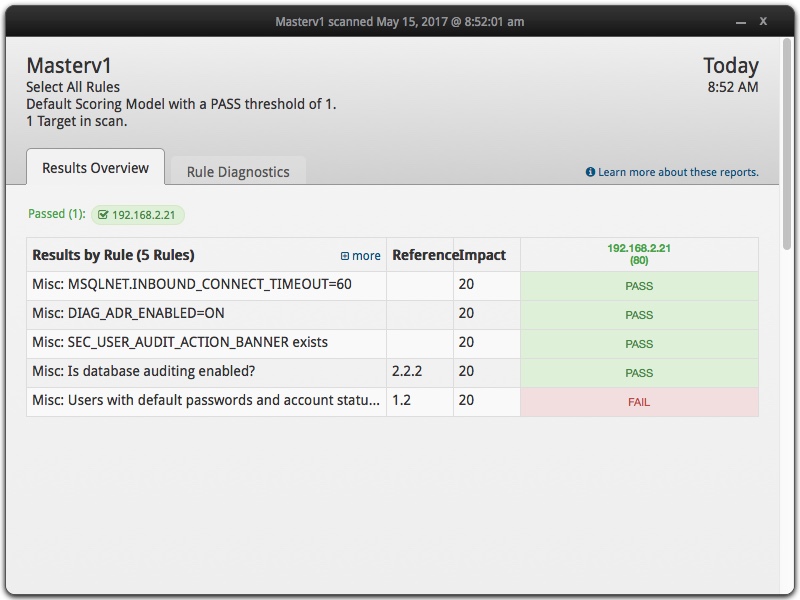
With a bit of experimentation (and great customer service from Joval), I was able to quickly prove I could develop OVAL content for automated SCAP scanning of Oracle databases, either for standard database security checks or for Oracle E-Business and/or PeopleSoft configurations. One key concern with the proof-of-concept is that connection string hardcodes the user name and password. The hardcoding is certainly a security issue, but JOVAL (as well as OpenSCAP) offers python bindings. The screen shot below is a single OVAL scan that included two SQL checks as well as checks against content in the sqlnet.ora file using the OVAL probe: textfilecontent54_test.
My OVAL definition is referenced below. I am providing it as an example for others. The key points you will know is for the JOVAL connection string for Oracle:
Engine: oracle
Version values: 11.2.0, 11.1.0, 10.2.0, 10.1.0, 9.2.0, 9.0.1
Connection string (do not use JDBC syntax): user=<username>;password=<password>;SID=<instance name>
If you want to replicate the proof-of-concept:
- Download a trial version of Joval Professional.
- Run a scan of your local laptop
- Run a remote scan of Linux server running your Oracle RDBMS
- Edit sample benchmark file (here) for your database
- Upload the edited sample benchmark into Joval
- Run the sample benchmark scan
What Next?
Having proven I can use OVAL to write Oracle and ERP audit checks, I will spend a bit more time expanding the POC. I am also interested in automation options for Joval and OpenSCAP exports to a NoSQL database such as MongoDB using the Asset Reporting Format (ARF) (https://scap.nist.gov/specifications/arf/). Both Joval and OpenScap have standard functionality to export results using ARF.
If you have any questions, please contact us at info@integrigy.com
References
Sample Oracle OVAL benchmark definition: SCAP OVAL Example Check for Oracle
SCAP
NIST SCAP site: https://scap.nist.gov/
SCAP content: https://nvd.nist.gov/ncp/repository?scap
Oracle Linux Security Guide – Using OpenSCAP: https://docs.oracle.com/cd/E37670_01/E36387/html/ol-scap-sec.html
Great summary of SCAP: https://energy.gov/sites/prod/files/cioprod/documents/Technical_Introduction_to_SCAP_-_Charles_Schmidt.pdf
OVAL
Writing OVAL content https://oval.mitre.org/documents/docs-07/Writing_an_OVAL_Definition.pdf
OVAL tutorial https://nvd.nist.gov/scap/docs/conference%20presentations/workshops/OVAL%20Tutorial%202%20-%20%20Definitions.pdf